Just as the internet has changed the way people communicate, work and learn, mobile technology has changed when, where and how consumers access information and entertainment. And smartphone use that goes beyond routine calls and text messages does not appear to be slowing, according to a Pew Research Center survey of U.S. adults conducted in July 2015.
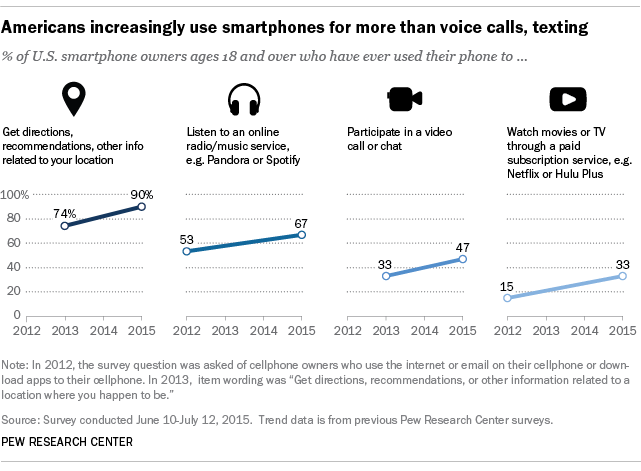
The percentage of smartphone owners who say they have ever used their phone to watch movies or TV through a paid subscription service like Netflix or Hulu Plus has doubled in recent years – increasing from 15% in 2012 to 33% in 2015.
Among the smartphone activities measured, getting location-based information is the most universal task. Nine-in-ten smartphone owners use their phone to get directions, recommendations or other information related to their location, up from 74% in 2013.
The share of smartphone users who report using their device to listen to online radio or a music service, such as Pandora or Spotify, or participate in video calls or chats has also increased by double digits in recent years. (2015 was the first year in which we surveyed about using a mobile device to buy a product online or get sports scores and analysis.)
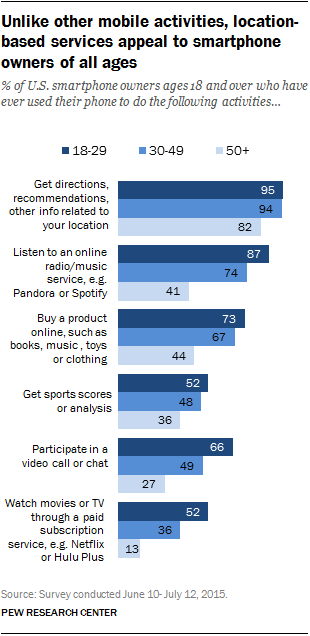
Younger adults are especially likely to reach for their phone for something other than calling and texting. Getting location-based information is the one activity measured that is common across all age groups, however.
Listening to music and shopping on the go are especially popular among smartphone owners ages 18 to 29: 87% have listened to an online radio or music service on their phone, compared with 41% of those 50 and over, and 73% have shopped online through their mobile device, versus 44% of older users.
Activities that are less prevalent but not uncommon among smartphone owners include video calling or chatting; getting sports scores or analysis; and watching movies or TV through a paid subscription service. Again, younger adults are especially likely to use their mobile device for all of these activities. For example, 52% of 18- to 29-year-old smartphone owners have ever used their phone to watch movies or TV shows through a paid subscription service, compared with 36% of 30- to 49-year-olds and only 13% of those 50 and older.
These differences speak to a broader pattern of younger Americans’ adoption of and engagement with technology. Younger adults are more likely than older adults to own a smartphone, to be constantly online and to rely on their smartphone for internet access.
To see more and the original story follow this link to Pew Research.