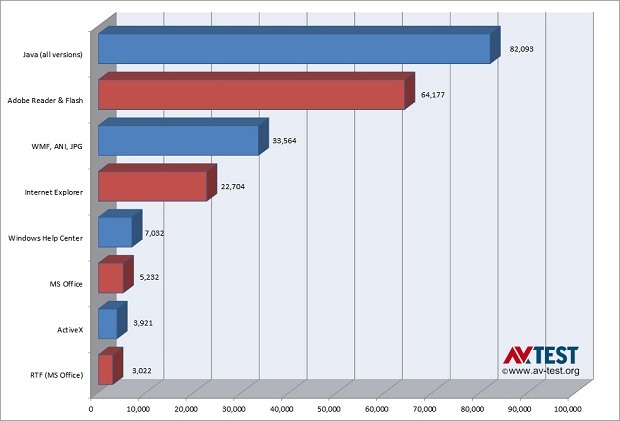
The ranking of insecure software according to the number of known exploit versions: A large number of vulnerabilities meant that Java, Adobe Reader and Flash were responsible for 66 percent of the exploit versions recorded between 2000 and 2013. Although other groups were also recorded, they are not presented in the ranking shown above.
From the year 2000 through today, Java, Adobe Reader and Flash were responsible for 66% of the vulnerabilities exploited by malware on Windows, according to a new study by the research group AV-Test Institute.
The study reinforces the well-known rule that keeping applications software up to date is of critical importance for system security. The study does not indicate how many of the exploits were active when the vulnerabilities were unpatched, but such exploits are undoubtedly a small percentage of the total.
The long time span of the study may make it more of historical interest than practical value. Within the last five to ten years both Adobe and Microsoft have improved their software development processes lowering the overall number of vulnerabilities and the severity of those that get through. Current versions of Windows and both Microsoft and Adobe applications, are far more secure than in 2000, or even 2008.
The same is not as true of Java, which is the biggest current problem of the programs tracked by the study, in part because so many users still have old versions of Java installed on their systems.
Other user practices, such as running as a standard user rather than as Administrator, also limit the severity of application exploits. This was a difficult practice to employ with Windows XP, but in current versions of Windows it is far more practical to run as standard user.
Source: ZD Net
